Flash briefs from cyber to cosmic. Mixing Tech, AI, quantum, biology, and art to ignite fresh angles and new perspectives.
Two papers, worlds apart—one mapping disease from cell-free DNA, the other decoding carbon ratios in the Milky Way—both arrive at similar methods. The real insight? Read beyond your field.
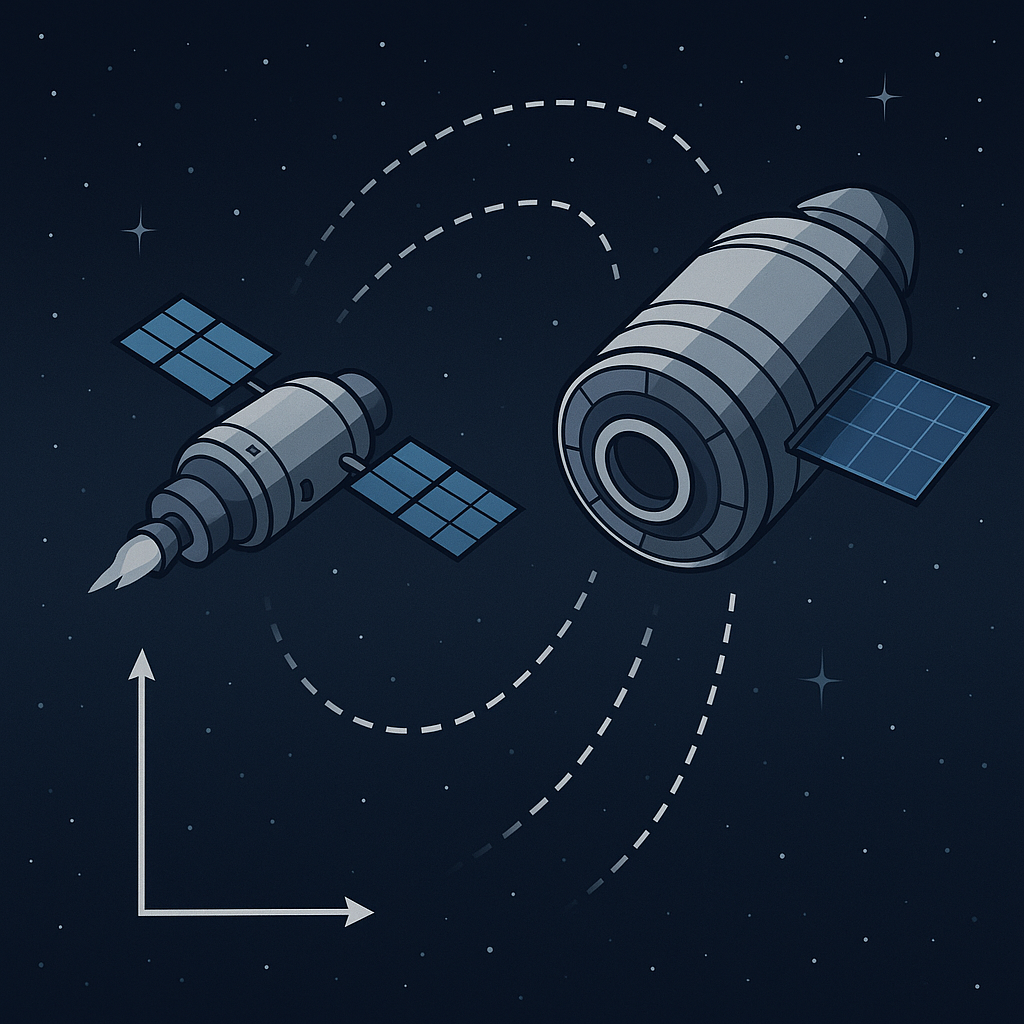
A new paper introduces a model predictive control (MPC) framework that guarantees real-time docking maneuvers for spacecraft, even under tight compute constraints. Here's how time-bounded optimization unlocks autonomy in orbit.
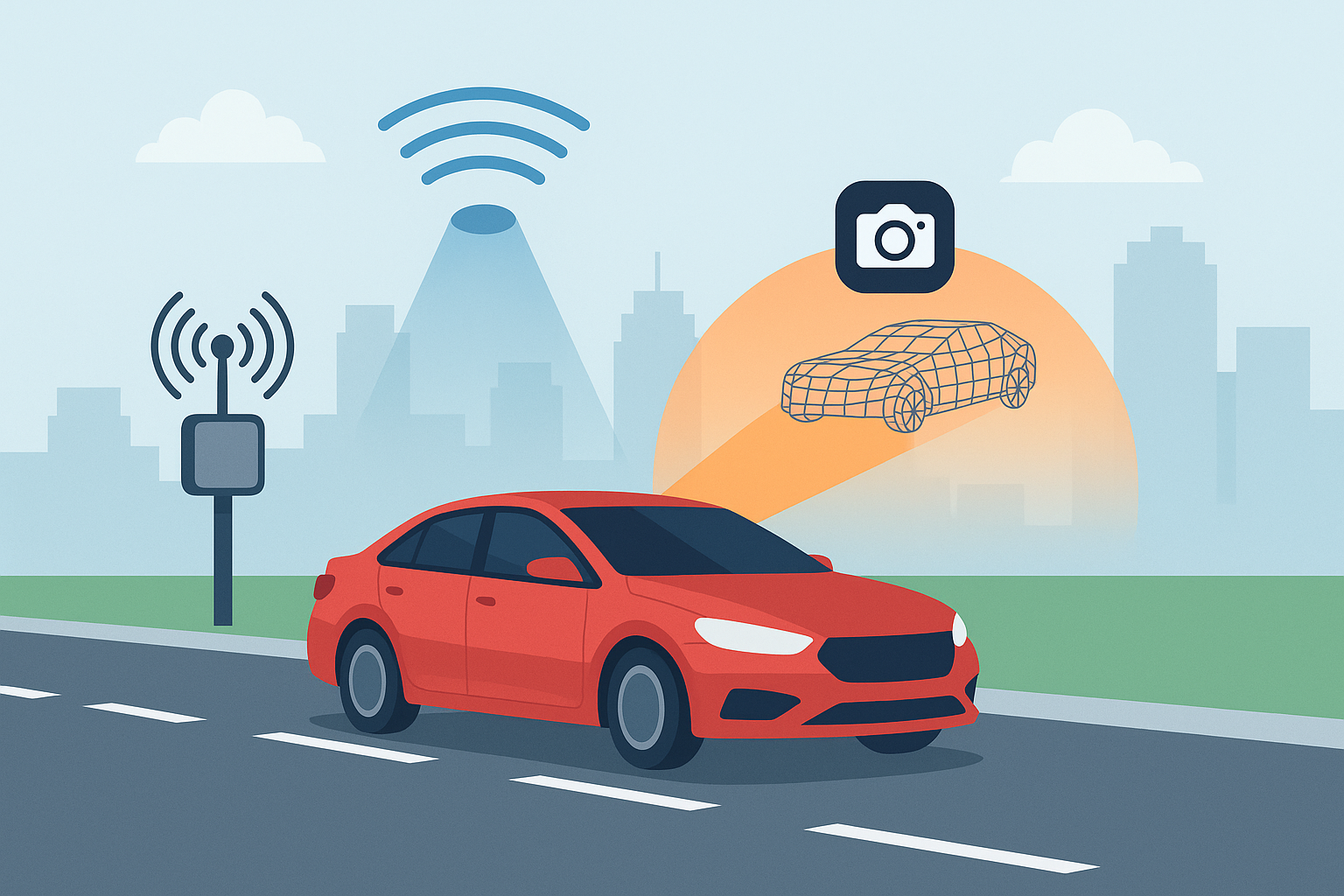
A new approach to vehicle-to-everything (V2X) networks fuses RF, vision, and LiDAR while compressing AI models for edge deployment. Here's how modality generation and lightweight design will shape 6G communications.
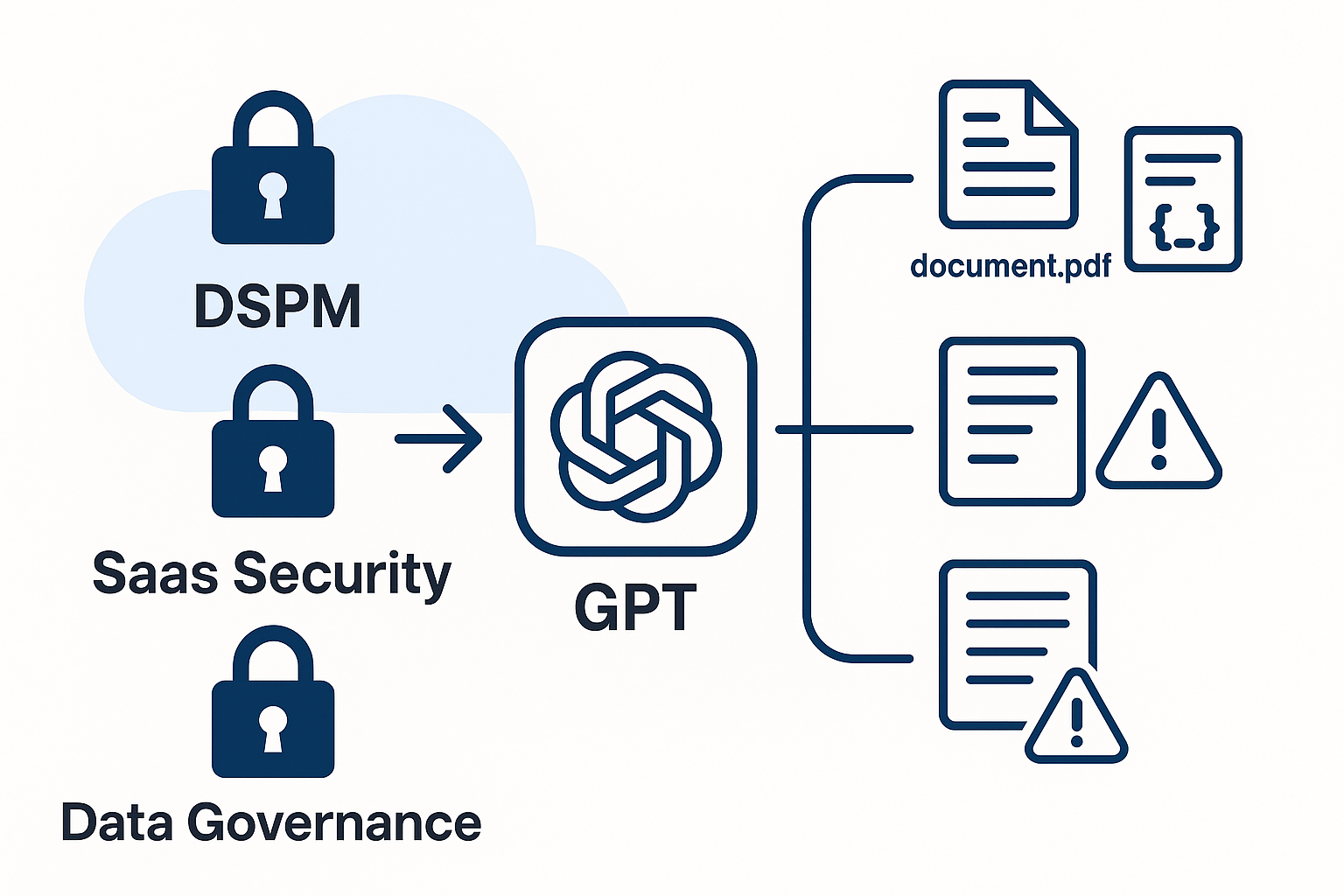
A new study reveals how GPTs can leak sensitive file data through five distinct vectors. Here's how experts in DSPM, SaaS security, and data governance can apply their skills to mitigate real-world LLM risks.